No audio available for this content.
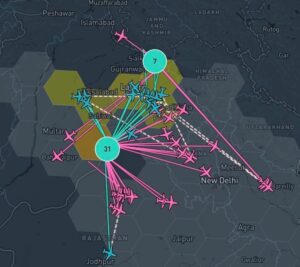
News outlet MSN has published a slideshow detailing seven take-aways from recent GNSS spoofing defense moves against Iranian missiles headed toward Israel. The missiles instead ended up in the Mediterranean Sea, apparently because of successful electronic hacking.
“The incident has caused tremors within the defense and cyber-defense communities, pointing to the mounting sophistication of electronic warfare and the weakness inherent in contemporary navigation systems,” the report states.
The event is being studied as a sophisticated method that “deceived” the missile’s guidance, making it continue on a reasonable course while deviating it from its targeted direction, an advance in electronic warfare that requires knowledge of the missile’s flight algorithms.
“Spoofing detection is much more difficult than jamming, since spoofed signals are made to mimic legitimate signals. Sophisticated detection techniques, like those employing pseudorange difference and sum sequence linearity, are being researched to separate genuine from spoofed GNSS signals. These detection techniques examine the consistency and conduct of signal measures, searching for minute discrepancies that indicate spoofing efforts.”
Spoofing is also affecting civilian sectors, such as when cargo ships collided in the Strait of Hormuz. The International Air Transport Association and the European Union Aviation Safety Agency have published a comprehensive plan to mitigate risks stemming from GNSS interference. The plan was part of the conclusions from a jointly hosted workshop on the topic of GNSS interference.
Agencies also are seeking reliable countermeasures as well as complementary PNT such as magnetic navigation.
See the MSN slideshow here.